ADB And Fastboot Command Compilation By OmBob
Disclaimer
Sideload Apps But Seen Installed From Playstore
adb install-multiple -i com.android.vending "AppName.apk" "ConfigA.apk" "ConfigB.apk"
- Gojek Driver
adb install-multiple -i com.android.vending .\com.gojek.partner.apk .\config.arm64_v8a.apk .\config.xxhdpi.apk - Grab Driver
adb install-multiple -i com.android.vending .\com.grabtaxi.driver2.apk .\config.arm64_v8a.apk .\config.xhdpi.apk - Shopee Food Driver
adb install-multiple -i com.android.vending .\com.shopee.foody.driver.id.apk .\config.arm64_v8a.apk .\config.xxhdpi.apk - Spark Driver
adb install-multiple -i com.android.vending .\com.walmart.sparkdriver.apk .\config.arm64_v8a.apk .\config.en.apk .\shopper.apk .\shopper.config.arm64_v8a.apk .\shopper.config.xxhdpi.apk .\config.xxhdpi.apk
supm install -i com.android.vending -r "Link2SD 4.3.1.apk"
Install all APK in the current folder
Powershell
Get-ChildItem -Filter *.apk | ForEach-Object { adb install $_.FullName }
CMD
for %f in (*.apk) do adb install "%f"
Install Modul Using Command Line On One Folder- adb shell
- su
- cd /sdcard/modul
- for f in *.zip; do
echo "Installing $f ..."
magisk --install-module "$f"
done
- adb shell
- su
- cd /sdcard/modul
- for f in *.zip; do
echo "Installing $f ..."
magisk --install-module "$f"
done
PowerShell command to install all .apks files
What it does:
-
Finds every
.apksfile in the current folder -
Copies it as a
.zipto a temp path -
Extracts it using PowerShell’s built-in
Expand-Archive -
Installs all
.apkfiles inside withadb install-multiple -
Deletes temp files afterward
Get-ChildItem -Filter *.apks | ForEach-Object {
$name = $_.BaseName
$temp = "$env:TEMP\$name"
$zip = "$env:TEMP\$name.zip"
Copy-Item $_.FullName $zip
Expand-Archive -Force $zip -DestinationPath $temp
Remove-Item $zip -Force
$apkPaths = (Get-ChildItem -Path $temp -Filter *.apk | ForEach-Object { $_.FullName })
if ($apkPaths.Count -gt 0) {
adb install-multiple -r -g $apkPaths
}
Remove-Item -Recurse -Force $temp
}
Bugjaeger Command
- fastboot devices
- fastboot flashing unlock
- fastboot flash boot [file_patch]
- fastboot reboot bootloader
- fastboot reboot
TWRP Command
- adb devices
- fastboot flash recovery
- fastboot reboot recovery
- adb shell
- twrp format data
- exit
- adb reboot recovery
- twrp wipe metadata
- twrp wipe dalvik
- twrp wipe cache
- adb push /path/to/your/rom.zip /sdcard/
- adb push /path/to/your/gapps.zip /sdcard/
- adb shell
- twrp install /sdcard/rom.zip
- twrp install /sdcard/rom.gapps.zip
- twrp format data
- reboot
Restore remove Sytem Apps
- adb shell
- su
- pm list packages -u | grep samsung
- cmd package install-existing com.samsung.android.app.smartcapture
- cmd package install-existing com.samsung.android.app.galaxyfinder
- reboot
SCRCPY
This tools really good for mirrorin your phone- scrcpy -w -S
Open mirror without wakeup the screen - scrcpy -m 1024
To limit both width and height to some maximum value - if you encounter always force closed
Message like "Could not open audio device: WASAPI can't find requested audio endpoint" you need this command scrcpy --no-audio
- scrcpy -w -S
Open mirror without wakeup the screen - scrcpy -m 1024
To limit both width and height to some maximum value - if you encounter always force closed
Message like "Could not open audio device: WASAPI can't find requested audio endpoint" you need this command scrcpy --no-audio
Copy File Using ADB
- folder
adb push .\apps2\ /sdcard/ - file
adb push myfile.zip /sdcard/
- folder
adb pull /sdcard/apps - file
adb pull /sdcard/services.jar
Disable Android Automatic Update
- adb shell pm disable-user --user 0 com.wssyncmldm
- adb shell pm disable-user --user 0 com.sec.android.soagent
- adb shell pm disable-user --user 0 com.transsion.ota
- adb shell pm disable-user --user 0 com.transsion.systemupdate
- adb shell pm disable-user --user 0 com.transsion.ota.tool
- adb shell pm disable-user --user 0 com.infinix.ota
- adb shell pm disable-user --user 0 com.infinix.xosupdater
- adb shell pm disable-user --user 0 com.android.updater
- adb shell pm disable-user --user 0 com.miui.systemAdSolution
- adb shell pm disable-user --user 0 com.xiaomi.mipicks
- adb shell pm disable-user --user 0 com.bbk.updater
- adb shell pm enable com.vivo.ota
- adb shell pm enable com.vivo.updater
- adb shell pm enable com.vivo.fota
- adb shell pm disable-user --user 0 com.android.dynsystem
- adb shell pm disable-user --user 0 com.oppo.ota
- adb shell pm disable-user --user 0 com.oplus.ota
- adb shell pm disable-user --user 0 com.coloros.ota
- adb shell pm disable-user --user 0 com.realme.ota
- adb shell pm disable-user --user 0 com.heytap.mcs
- adb shell pm uninstall -k –user 0 org.pixelexperience.ota
Disable Update & Secure Pay/ Check On Realme & Oppo
adb shell pm disable-user --user 0 com.coloros.securepayadb shell pm uninstall -k --user 0 com.oppo.otauiadb shell pm disable-user --user 0 com.realme.securitycheckadb shell pm disable-user --user 0 com.realme.securitycheck
If you want to reinstall the OTA service, just do :adb shell cmd package install-existing com.oppo.ota cmd package install-existing com.oppo.otaui
Magisk
Install Modul Using Command Line- adb shell
- su
- /sdcard/apps2/
- magisk --install-module mymodule.zip
- reboot
- adb shell
- su
- /sdcard/apps2/
- magisk --install-module mymodule.zip
- reboot
Remove Magisk Modules Using CMD
You can use this command if you have enable usb debugging before, without TWRP. Run the command from the bootloop status
adb wait-for-device shell magisk --remove-modules
Whitelist On Magisk
Shamiko
NoHello
This will make magisk automatic block all root acces. Make sure to install shamiko module before.adb shellsumkdir /data/adb/nohello/whitelist
Magisk specific checks Root Detection
Pull Partition From Android Device
- dd if=/dev/block/by-name/boot of=/sdcard/boot.img
- dd if=/dev/block/by-name/vbmeta of=/sdcard/vbmeta.img
- dd if=/dev/block/by-name/boot of=/sdcard/boot.img
- dd if=/dev/block/by-name/vbmeta of=/sdcard/vbmeta.img
- dd if=/dev/block/by-name/boot_a of=/sdcard/boot_a.img
- dd if=/dev/block/by-name/boot_b of=/sdcard/boot_b.img
- dd if=/dev/block/by-name/vbmeta_a of=/sdcard/vbmeta_a.img
- dd if=/dev/block/by-name/vbmeta_a of=/sdcard/vbmeta_b.img
- dd if=/dev/block/by-name/boot_a of=/sdcard/boot_a.img
- dd if=/dev/block/by-name/boot_b of=/sdcard/boot_b.img
- dd if=/dev/block/by-name/vbmeta_a of=/sdcard/vbmeta_a.img
- dd if=/dev/block/by-name/vbmeta_a of=/sdcard/vbmeta_b.img
Reinstall_failed_verification_failure
When you encounter this message, its mean your just extract just one apk, but the apps instead of several apk (split). To solve this you need extract all of the split APK using MT manager/ lucky p4tcher
Script To Enable Untrust touch
When you need to overlay but android system block, you can run this script to disable it To allow untrusted touches (root needed) you can run using termux or MT manager
su -c settings put global block_untrusted_touches 0
Restore Deleted File On Android
Accidentally delete your file on android? No worries it still there, just just can see it. You can navigate to this trash folder using adb or android file manager
cd /mnt/runtime/full/emulated/0/Android/.Trash/
Play Integrity Fix
To pass Device verdicts (legacy and new) by default without forging a valid certificate chain, you must run this command as root.
sed -i 's/"spoofVendingSdk": 0/"spoofVendingSdk": 1/'/data/adb/modules/playintegrityfix/pif.json
Show Lsposed Menu on Android 10 Samsung
So you allready install lsposed modul it work. And you also already install modul but still lsposed menu doesn't show? This is the solution. Or Simply you can use irena lsposed can open the lsposed command from trigger button (need magisk kitsune 27.xx or alpha 28.xxx or higher)- adb shell
- su
- su -c am start-activity -a android.intent.action.MAIN -p com.android.shell -n com.android.shell/.BugreportWarningActivity -c org.lsposed.manager.LAUNCH_MANAGER
- It will automaticle shown lsposed menu
- enable the shortcut menu
- adb shell
- su
- su -c am start-activity -a android.intent.action.MAIN -p com.android.shell -n com.android.shell/.BugreportWarningActivity -c org.lsposed.manager.LAUNCH_MANAGER
- It will automaticle shown lsposed menu
- enable the shortcut menu
Acess Lsposed Menu Using Dialer
You can use this method for Xiaomi, Infinix, Realme, Oppo, Vivo, etc except Samsung
- open dialer
- type *#*#5776733#*#*
- open dialer
- type *#*#5776733#*#*
Using Custom DPI On Full HD
If you were using a custom DPI on FULL HD, for example ⏩You're using 400 or 380 or 370 on 1080x1920 FHD ResolutionDo these to properly change resolution to avoid getting the UI or Icons Bigger than Normal.
Example;If you are using 400 DPI on 1080x1920FHD.
400÷3=133 DPI400-133=267 DPI Switch Slot
case : You cannot boot into android after flash buildROM, eg Note 10 5G cammelian
fastboot set_active a
Switch Slot
case : You cannot boot into android after flash buildROM, eg Note 10 5G cammelian
fastboot set_active aFix Email Logout
Some custom ROM experience strange event, that is logout email and cannot login back. Run this command from termux or adb. Need root acces or run from custom recovery- rm /data/system_ce/0/accounts_ce.db
- rm /data/system_de/0/accounts_de.db
- rm /data/system/sync/accounts.xml
- rm /data/system_ce/0/accounts_ce.db
- rm /data/system_de/0/accounts_de.db
- rm /data/system/sync/accounts.xml
LZ4 Command Line
Some usefull lz4 command, you get the apps from here- Compress same size as samsung lz4
lz4 -B6 --content-size system.img - Decompress and unpack a directory and its contents:
lz4 -dc dir.tar.lz4 | tar -xv - Package and compress a directory and its contents:
tar cvf - path/to/directory | lz4 - dir.tar.lz
- Compress same size as samsung lz4
lz4 -B6 --content-size system.img - Decompress and unpack a directory and its contents:
lz4 -dc dir.tar.lz4 | tar -xv - Package and compress a directory and its contents:
tar cvf - path/to/directory | lz4 - dir.tar.lz
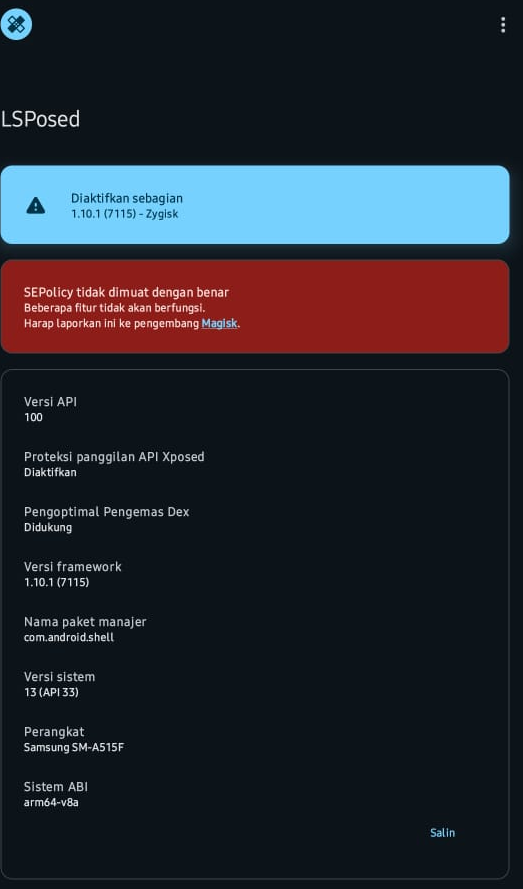
LSPosed Partially Activated
Solution 1 Lsposed is broken- Disabling the lsposed module from magisk
- Rebooting
- Enabling the lsposed module
- Reboot
- Disabling the lsposed module from magisk
- Rebooting
- Enabling the lsposed module
- Reboot
Solution 2 Conflict with some module- After turning off all modules
- turning on only LSPosed
- reboot
- Enable one by one module, check where the modul conlict
- After turning off all modules
- turning on only LSPosed
- reboot
- Enable one by one module, check where the modul conlict
Dangerous Props (Rootbeer)
It is reported on some phone, either stock or custom ROM (Mi A1, LineageFE, etc). Show Dangerous Prop. This is the solution (you must have root acces)
- adb root
- adb remount
- adb shell
- mount -o rw,remount /
- nano /system/build.prop
- ro.secure=0 # should be 1
- ro.debuggable=1 # should be 0
- ro.build.type=userdebug" # should be "user"
additionally in order to pass the "test keys" check, one can replace the "test-keys" with "release-keys" on build.prop
- adb root
- adb remount
- adb shell
- mount -o rw,remount /
- nano /system/build.prop
- ro.secure=0 # should be 1
- ro.debuggable=1 # should be 0
- ro.build.type=userdebug" # should be "user"
Whatsapp Database Location
- Android 10 : Penyimpanan bersama internal\WhatsApp\Databases
- Android 11 Up : Android\media\com.whatsapp\WhatsApp\Databases
- WA businnes : Android\media\com.whatsapp.w4b\WhatsApp Business\Databases
Android\media\com.whatsapp\WhatsApp\Databases
- Android 10 : Penyimpanan bersama internal\WhatsApp\Databases
- Android 11 Up : Android\media\com.whatsapp\WhatsApp\Databases
- WA businnes : Android\media\com.whatsapp.w4b\WhatsApp Business\Databases
Android\media\com.whatsapp\WhatsApp\Databases
Enable cam2api (gCam)
You can run this command from adb or custom recovery (need root acces)- adb shell
- su
- setprop persist.camera.HAL3.enabled 1
- setprop persist.vendor.camera.HAL3.enabled 1
- setprop persist.camera.stats.test 5
- setprop persist.vendor.camera.stats.test 5
- setprop persist.camera.eis.enable 1
- adb shell
- su
- setprop persist.camera.HAL3.enabled 1
- setprop persist.vendor.camera.HAL3.enabled 1
- setprop persist.camera.stats.test 5
- setprop persist.vendor.camera.stats.test 5
- setprop persist.camera.eis.enable 1
Disable cam2api (gCam)
Sometime you need this, if you failed to do face verification on some apps like Grab Driver- adb shell
- su
- setprop persist.camera.HAL3.enabled 0
- setprop persist.vendor.camera.HAL3.enabled 0
- adb shell
- su
- setprop persist.camera.HAL3.enabled 0
- setprop persist.vendor.camera.HAL3.enabled 0
Speedup Windows
If you have poor RAM and HDD only, windows will make you missery. Simply remove defender & MS Edge to make you computer usable!
Disable Driver Signature
- Full power off > go to BIOS> find disable secure boot > save reboot
- start > run > type cmd
- Right click > Run as administrator
- bcdedit /set testsigning on
- restart computer
Lock Bootloader From Fastboot
- fastboot oem lock ⏩ Xiaomi
- fastboot flashing lock ⏩ Trans/ Realme
Android Product Out Not Set
Make Android Partition Writeable
- adb shell
- mount -o remount,rw /system_root
- adb push .\services.jar /system_root/system/framework/
- mount -o remount,rw /
- mount -o remount,rw /odm
- mount -o remount,rw /product
- mount -o remount,rw /system_ext
- mount -o remount,rw /vendor
Disable Security Log Agent Notification
- adb shell
- su
- cd /system/app/SecurityLogAgent
- mv SecurityLogAgent.apk SecurityLogAgent.apk.bak
Install APK From Android Using Shell
- copy apk to /data/local/tmp
- rename to file into x.apk e.g
- pm install -r -t --force-queryable x.apk
Downgrade APK Without Uninstall APK
Realme | Pull Image From Stock Recovery
Boot into stock recovery, then plug your device into computer, Type follow commands :
adb rootadb pull /dev/block/by-name/boot boot.img
For Dynamic Partition
adb pull /dev/block/by-name/boot_a boot1.img
It will save your boot image to current folder. SAME FOLLOWS FOR PULLING OTHER IMG FILES
JUST REPLACE boot.img to vbmeta.img or others
Nikel Remove & Restore Google System Framework
start with type adb shell
- Search for package
pm dump com.google.android.gsf | grep path - Remove Package
pm uninstall -k --user 0 com.google.android.gsf - Reinstall package
pm install -r --user 0 /system/priv-app/GoogleServicesFramework/GoogleServicesFramework.apk
Install / get back uninstalled Apps (APKs) with ADB
get the path for that app
- 1st method
adb shell pm uninstall -k --user 0 com.android.updater
adb shell cmd package install-existing com.android.updater - 2nd method
adb shellpm dump com.android.updater | grep path
pm install -r --user 0 /system/app/Updater/Updater.apk
Decrypt Manually
- Copy /vendor/etc/fstab.**** over to another folder.
- Edit it to remove the line containing the word "encryption"
- Boot into twrp
- Use twrp file manager to replace the fstab file with the edited one.
- Format data (not just wipe)
- Reboot to recovery
- Reboot to system
- Setup the phone completely
- Reboot to twrp
- Backup boot data and super
Fix Magisk lag
Download magisklagfix.sh
use terminal emulator (android) or use terminal in pc (windows/linux)
- su
- mkdir -p /data/adb/service.d && cp /sdcard/magisklagfix.sh /data/adb/service.d/ && chmod +x /data/adb/service.d/magisklagfix.sh
tail message in Android
# adb shell cat /proc/kmsg
Force Permission On Android Go (Root)
- adb shell
- su
- Enable Floating Window
pm grant com.grabtaxi.driver2 android.permission.SYSTEM_ALERT_WINDOW - Allow All the Time
pm grant co.talenta android.permission.ACCESS_BACKGROUND_LOCATION
Fix DM Verity Corruption
Oppo Engginer Mode Code
*#899#
Remove Infinix Bloatware
-
adb shell pm uninstall -k --user 0 com.transsion.phonemaster -
adb shell pm uninstall -k --user 0 com.transsion.plat.appupdate -
adb shell pm uninstall -k --user 0 com.transsion.wifiplaytogether -
adb shell pm uninstall -k --user 0 com.transsion.systemupdate
Realme/ Oppo Remove Bloatware
adb shell pm uninstall -k --user 0 com.oppo.otaadb shell pm uninstall -k --user 0 com.jakarta.baca.liteadb shell pm uninstall -k --user 0 com.heytap.quickgameadb shell pm uninstall -k --user 0 com.heytap.browseradb shell pm uninstall -k --user 0 com.heytap.marketadb shell pm uninstall -k --user 0 com.heytap.mall
New Oppo
adb shell pm uninstall -k --user 0com.redteamobile.roamingadb shell pm uninstall -k --user 0com.oplus.otaadb shell pm uninstall -k --user 0com.heytap.pictorialadb shell pm uninstall -k --user 0com.heytap.musicadb shell pm uninstall -k --user 0com.coloros.musiclink (failed)adb shell pm uninstall -k --user 0com.nearme.gamecenter (failed)adb shell pm uninstall -k --user 0com.oplus.gamesadb shell pm uninstall -k --user 0
Samsung
- adb shell
pm uninstall -k --user 0 com.samsung.android.securitylogagent -
adb shell pm uninstall -k --user 0 com.sec.android.soagent adb shell pm uninstall -k --user 0 com.wssyncmldm
Install apk from local but seen as from playstore
adb install -i com.android.vending -r "Link2SD 4.3.1.apk"
Remove Google Bloatware
adb shellpm uninstall -k --user 0 com.google.android.apps.photosadb shellpm uninstall -k –user 0 com.google.android.apps.tachyonadb shellpm uninstall -k –user 0 com.google.android.apps.docsadb shellpm uninstall -k –user 0 com.google.android.apps.subscriptions.redadb shellpm uninstall -k –user 0 com.google.android.musicadb shellpm uninstall -k –user 0 com.google.android.videosadb shellpm uninstall -k –user 0 com.google.android.feedbackadb shellpm uninstall -k –user 0 com.android.browseradb shell pm uninstall -k --user 0com.google.android.apps.nbu.filesadb shell pm uninstall -k --user 0com.google.android.apps.chromecast.appadb shell pm uninstall -k --user 0com.google.android.keep
Remove Xiaomi Bloatware
-
adb shellpmpm uninstall -k –user 0 com.mi.android.globalminusscreen adb shell pm pm uninstall -k --user 0 com.mi.globalbrowser-
adb shellpmpm uninstall -k –user 0 com.miui.analytics -
adb shellpmpm uninstall -k –user 0 com.miui.cleanmaster -
adb shellpmpm uninstall -k –user 0 com.miui.compass -
adb shellpmpm uninstall -k –user 0 com.miui.notes -
adb shellpmpm uninstall -k –user 0 com.miui.player -
adb shellpmpm uninstall -k –user 0 com.miui.weather2 -
adb shellpmpm uninstall -k –user 0
Hide apps
adb shellpm hide com.example.packagenameadb shellpm unhide com.example.packagename
Remove apps
adb uninstall com.android.calculator2 List Package
adb shellsu 0pm list packages
Disable vbmeta
- fastboot flash --disable-verity --disable-verification vbmeta vbmeta.img
Download Mode Using ADB
- Samsung adb reboot download
- adb to download mode (xiaomi eg. mi4c)
- fastboot oem edl
- adb reboot edl
Flash Modem
fastboot flash modem NON-HLOS.bin
Getting information about phone
fastboot getvar all
fastboot getvar product
fastboot -i 0x17ef oem device-info (lenovo)
adb command to fastboot
adb reboot bootloader
adb command to recovery
adb reboot recovery
unlock bootloader
fastboot oem unlock-go
fastboot -i 0x17ef oem unlock-go (lenovo)
check Bootloader Status
fastboot oem device-info
FLASH SYSTEM.IMG
fastboot flash system system.img
Flash Recovery
fastboot flash recovery images.img
Boot from images
fastboot boot twrp.img
Shutdown from ADB
adb shell reboot -p








Post a Comment for "ADB And Fastboot Command Compilation By OmBob"
Post a Comment